The Australian Cyber Security Centre, recorded an astounding 76,000 cybercrime reports, signifying a significant 13% surge compared last fiscal year.
In light of these threats, mitigating risks becomes paramount. Implementing robust security measures and fostering a corporate culture that places a strong emphasis on cybersecurity awareness are essential steps in safeguarding a business.
These comprehensive cybercrime statistics not only shed light on the current landscape of cyber threats in Australia but also delve into the most prevalent tactics employed by cybercriminals.
By staying well-informed about the latest trends and statistical insights, you can empower your organisation with the necessary tools and knowledge to shield itself against potential cyber threats effectively.
Top Cyber Threat Statistics 2022
- The Australian Cyber Security Centre (ACSC) registered a staggering 76,000 cybercrime reports in the latest annual report, marking a substantial increase of nearly 13% compared to the previous fiscal year.
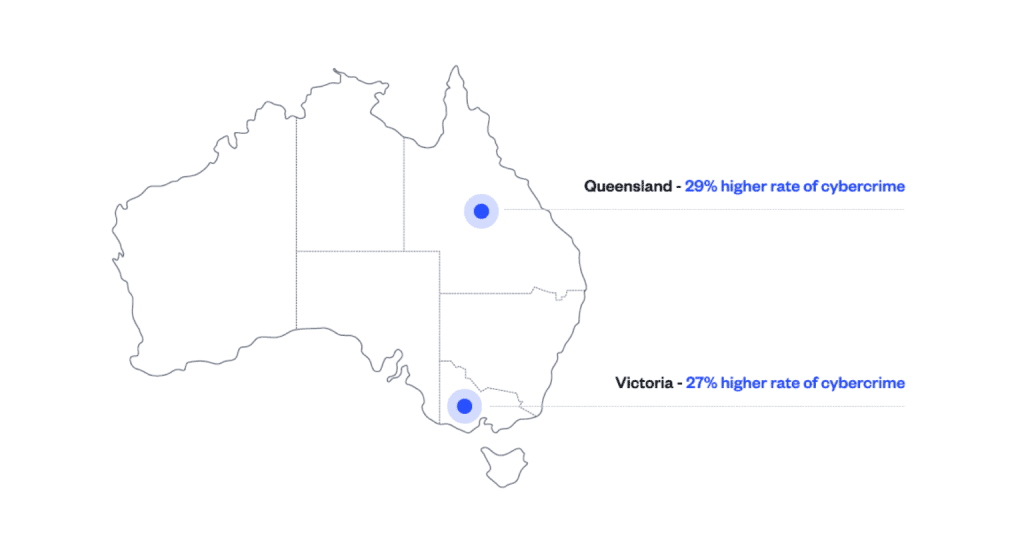
- In the period spanning 2021-2022, Queensland and Victoria reported notably higher rates of cybercrime, accounting for 29% and 27% of the total incidents, respectively, relative to their populations.
- Cybercrime continues its upward trajectory, with the fourth quarter of 2021 seeing an unprecedented surge in cyberattack attempts, reaching an all-time high.
- The average cost per cybercrime report has seen a significant rise, reaching over $39,000 for small businesses, $88,000 for medium-sized businesses, and exceeding $62,000 for large enterprises, indicating an average increase of 14%.
- Ransomware attacks have experienced an alarming surge of nearly 500% since the onset of the COVID-19 pandemic, underscoring the growing threat landscape.
Annual Cyber Threat Report for 2022
- According to the Annual Cyber Threat Report for 2022, the Australian Cyber Security Centre (ACSC) recorded an uptick in cybercrime reports, exceeding 76,000 cases, marking a nearly 13% surge compared to the previous fiscal year.
- Throughout the 2021-2022 financial period, Australia witnessed a surge in sophisticated cyber threats such as extortion, corporate espionage, and fraud. The frequency of these reports increased from one every 7 minutes in the previous financial year to one every 8 minutes.
- The Australian Cyber Security Centre reported a notable increase in cybercrime cases from 2020 to 2021, with a rise of almost 13%. During this period, over 67,500 cybercrime reports were filed, representing a 13% increase compared to 2019.
- This surge in cybercrime reporting translated to a cyber attack being reported every 8 minutes, a significant shift from the previous rate of one every 10 minutes in 2019.
- In the fiscal year 2021-2022, Queensland (29%) and Victoria (27%) registered disproportionately higher rates of cybercrime relative to their respective populations.
- Additionally, the Northern Territory saw the highest average reported losses, exceeding $40,000 per cybercrime report.
The most frequently reported cybercrimes across Australia included online fraud (27%), online shopping-related incidents (14%), and online banking-related issues (13%). Furthermore, the prevalence of ransomware attacks continued to grow during this period.
AU – Cyber Security Strategy
In December 8, 2022, the Honorable Clare O’Neil MP, the Minister for Cyber Security, unveiled plans for the creation of the 2023-2030 Australian Cyber Security Strategy, often referred to as “the Strategy.”
The cyber strategy aims to align with the Australian Government’s vision of positioning Australia as the world’s premier cyber-secure nation by 2030.
This will involve the Australian Government taking the lead in orchestrating a nationwide, coordinated effort to enhance Australia’s cyber security and overall resilience.
The Government is currently formulating cyber security policies and initiatives across four primary domains:
- Fostering a secure economy and a flourishing cyber ecosystem.
- Ensuring the security and resilience of critical infrastructure and government operations.
- Establishing a self-reliant and assured capability to counter cyber threats.
- Positioning Australia as a trusted and influential global leader in cyber security, fostering partnerships with neighboring countries to elevate cyber security standards and promote the development of a cyber-resilient region.
The Increasing Prevalence Of Cyber Threats
In 2023, the Australian Government places significant emphasis on addressing the growing prevalence of cyber threats, underscoring the importance for both businesses and individuals to prioritize cyber security.
In a late 2022 National Press Club address, O’Neil unveiled a range of fresh initiatives aimed at enhancing cyber security nationwide.
These initiatives have been strategically crafted to safeguard not only the government but also businesses and individuals against the ever-increasing risk of cyberattacks.
Forthcoming initiatives are poised to advance us toward a more robust cybersecurity posture, serving as a safeguard for the government, businesses, and individuals against cyberattacks, data breaches, and various other online perils.
The events of 2022 served as a stark reminder that our vulnerability remains pronounced without a heightened emphasis on cyber security within both the private sector and government.
O’Neil MP, also committed to implementing proactive measures aimed at elevating cyber security awareness, engagement, and regulatory standards nationwide.
Cyber Security Jobs
More than 1 million cyber security jobs will be available by 2023, but less than 400,000 cybersecurity professionals will be trained by then.
The field of cybersecurity is experiencing continuous expansion, and its growth is poised to have a significant impact on job opportunities in Australia.
Projections indicate that in 2023, the cybersecurity industry is expected to grow by 11%, followed by a remarkable surge of 20% by 2025.
These growth figures are not just statistics; they represent a burgeoning demand for cybersecurity professionals in Australia.
The escalating need for robust cybersecurity measures translates into a wealth of career prospects for individuals interested in this dynamic field.
Online Fraud In Australia
Australain cybercrime statistics for the period 2021-2022 indicated online fraud (27%), online shopping-related incidents (14%), and online banking-related issues (13%). Furthermore, the prevalence of ransomware attacks continued to grow during this period
What Are The Predictions For Cybersecurity In 2024?
Predictions suggests that by 2024 attackers will have shifted away from exploiting known vulnerabilities toward targeting business processes directly through social engineering attacks like phishing or malware campaigns designed specifically to target certain industries or regions
5 Top Global Cyber Threats in 2023
As the cybersecurity landscape continues to change, so do the threats organizations need to worry about.
With 74% of security decision-makers reporting that their organisation’s sensitive data may have been potentially compromised or breached in the last 12 months, it’s pretty apparent no one is immune to cyber-attacks.
While ransomware and Business Email Compromise (BEC) aren’t going away anytime soon, there are a few new threats on the block you should be aware of. Forrester breaks down the top five threats to look for in 2023 in their latest report.
- Ransomware
Guess who was surprised to see ransomware on this list? The correct answer is no one, which is why your organisation needs to focus on ways to prevent it. From Security Awareness Training (SAT) to intelligent email security solutions, make sure you’re prepared as this threat isn’t going away anytime
soon.
- BEC/Social Engineering
After $43 billion in losses, BEC is once again the number one cybercrime in reported losses according to the FBI. From romance scams to social engineering attacks
- Artificial Intelligence
Advances in AI and Machine Learning (ML) algorithms like ChatGPT opens an entirely new world of threats to organisations. This emerging technology is only scratching the surface of its potential, so we need to keep a keen eye on this.
- Cloud Computing
Insecure configurations continue to be a top concern for organisations around the world which can lead to sensitive data breaches.
- Geopolitical
From the Russia-Ukraine conflict to potential sanctions and bans of Chinese technology, this everchanging climate is something we must all keep our eyes on.
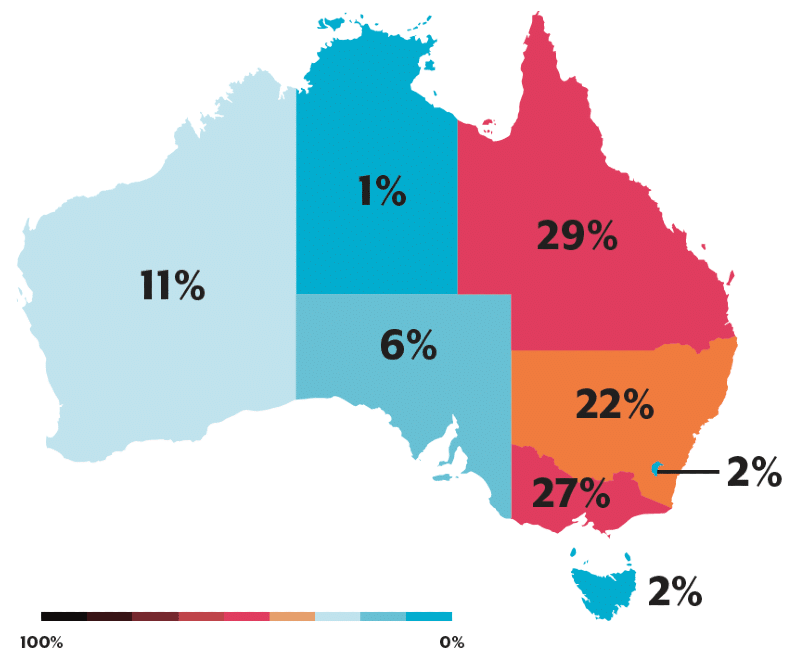
Cybercrime Reports By State & Territory
Australia’s more populous states continue to report more cybercrime. Queensland and Victoria report disproportionately higher rates of cybercrime relative to their populations.
However, the highest average reported losses were by victims in the Northern Territory (over $40,000 per cybercrime report where a financial loss occurred) and Western Australia (over $29,000).
Cybercrime By Type
The most frequently reported cybercrimes were all cyber enabled crimes:
- online fraud: approximately 27 per cent
- online shopping: approximately 14 per cent
- online banking: approximately 13 per cent.
Online fraud is a prevalent cybercrime type, accounting for roughly 27 percent of reported incidents. Online shopping experiences a substantial share of cybercrimes as well, making up approximately 14 percent of the total.
Meanwhile, online banking also faces its fair share of threats, constituting around 13 percent of reported cybercrime incidents underscoring the need for heightened cybersecurity measures to safeguard digital transactions, investments and financial activities.
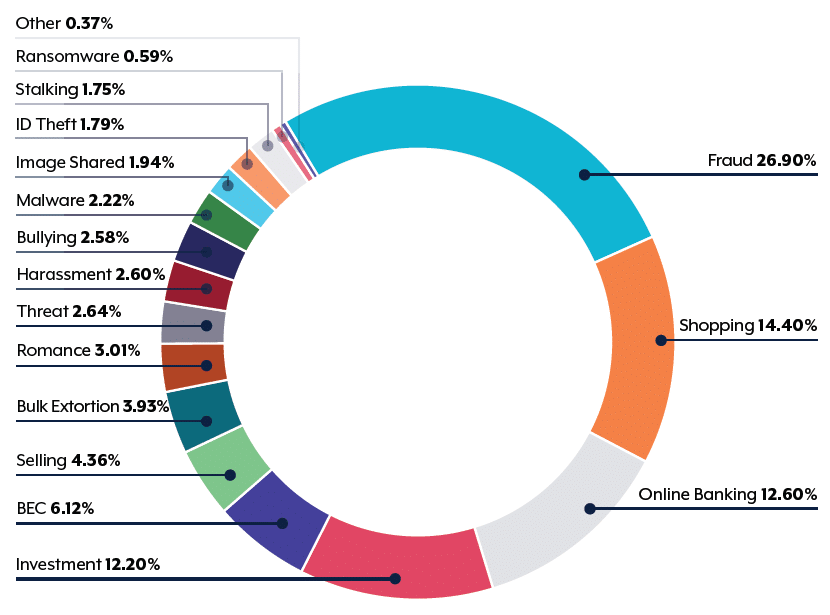
Cyber dependent crimes, such as ransomware, were a very small percentage of total cybercrime reports. Nevertheless, the ACSC assesses that ransomware remains the most destructive cybercrime threat.
Ransomware has a dual impact on victim organisations—their business is disrupted by the encryption of data, but they also face reputational damage if stolen data is released or sold on. The public are also impacted by disruptions and data breaches resulting from ransomware.
Cybercrime Loss By Organisation Size
Medium-sized businesses, as defined by the Australian Bureau of Statistics (comprising 20 to 199 employees), experienced the highest average financial loss per cybercrime incident reported.
This can be attributed to their comparatively lower adoption of cybersecurity measures outlined in the ACSC’s Strategies to Mitigate Cyber Security Incidents. These strategies play a crucial role in reducing the likelihood and impact of cyber incidents.
Moreover, medium-sized enterprises are more inclined to report cybercrimes, as they often lack comprehensive in-house or commercial incident response capabilities, a feature more commonly found in larger organisations.
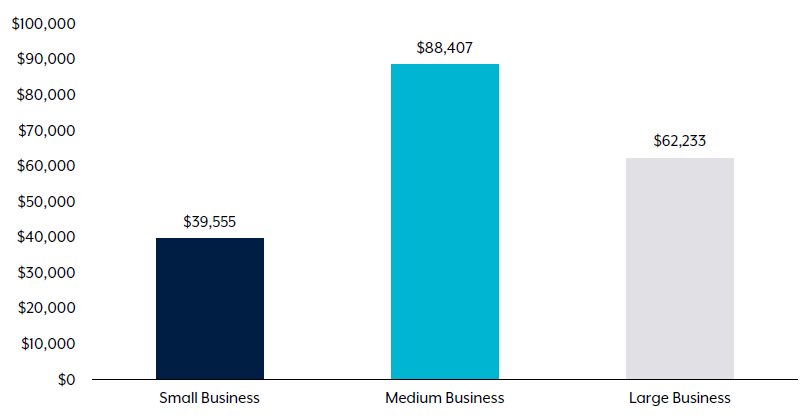
The ACSC has strongly encouraged all organisations to report cybercrimes, irrespective of the financial loss incurred.
This will contribute to a more comprehensive understanding of the threat landscape and enhances our collective ability to defend against cyber threats.
The Foothold To Steal Australia’s Secrets
In the fiscal year 2021–22, state actors persisted in conducting malicious cyber operations, effectively utilizing these tactics for political and economic espionage.
These state actors actively pursue sensitive information, including personally identifiable information (PII), to support their government’s intelligence objectives. However, their interests extend beyond classified data; they also seek to comprehend our identities, connections, and core values.
In certain instances, they may aim to establish a strategic presence within networks as a prelude to potential coercive or disruptive actions against us.
Throughout the past financial year, Australia remained a consistent target of sustained cyber espionage by a diverse array of state actors. This is primarily due to Australia’s regional and global interests, its involvement in international partnerships, and active participation in multilateral forums.
Cyber espionage activities are often conducted or overseen by foreign intelligence services, which target public and private networks across Australia.
The networks encompass political, diplomatic, military, technological, commercial, and personal data belonging to individual Australians.
The Australian Cyber Security Centre (ACSC) collaborated closely with various Australian government agencies at both state and territory levels to bolster the resilience of critical events, such as the Census and state and federal elections, against malicious cyber activities orchestrated by state or criminal actors.
Cyber Risks For Aussie Networks
Russia’s invasion of Ukraine underscored the tangible danger posed by disruptive and destructive cyber operations, including the potential for unintended harm to third parties.
Some of Russia’s cyber actions had repercussions that extended beyond their primary targets. An illustrative example occurred on February 24, 2022, when an attack was launched against a satellite communications company.
The assault not only caused disruptions within Ukraine but also had spillover effects that affected more than 10,000 satellite communications terminals located outside Ukraine.
These terminals played crucial roles in supporting the operation of wind turbines and providing internet services to private citizens in various geographic regions.
Previous cyberattacks against Ukraine have likewise yielded international ramifications, such as the NotPetya malware incident in 2017, which impacted companies globally, including entities in Australia.
Russian cyber actors have, on occasion, engaged in malicious activities in response to military support provided by the United States, the United Kingdom, Australia, and other allied nations, as well as in response to economic sanctions imposed on Russia.
Australia’s vulnerability in future regional or global conflicts extends to potential cyber operations targeting the supply chains upon which Australian systems rely.
The vulnerability persists even if Australia is not directly involved in the conflict, and the onset of such disruptions may offer little to no advance warning.
Owners of Australian networks need to contemplate how to fortify their critical systems and safeguard sensitive information, potentially through enhanced segmentation between corporate and operational networks.
Cybercrime-as-a-Service – (CaaS)
The proliferation of Cybercrime-as-a-Service (CaaS) continues to amplify the overall cybercrime threat faced by Australia. CaaS encompasses a widening spectrum of purchasable tools, services, and information designed to facilitate cybercriminal activities.
Examples of CaaS offerings encompass, but are not confined to, the provision of server infrastructure for hosting cybercriminal campaigns, the sale of access to compromised victim networks, services for money laundering, and the development and obfuscation of malware.
The availability of these enabling functions eliminates the need for individual actors to excel in every aspect of a criminal operation. In essence, cybercriminals are subcontracting various elements of their operations, fueling the growth of an underground marketplace tailored to meet their requirements.
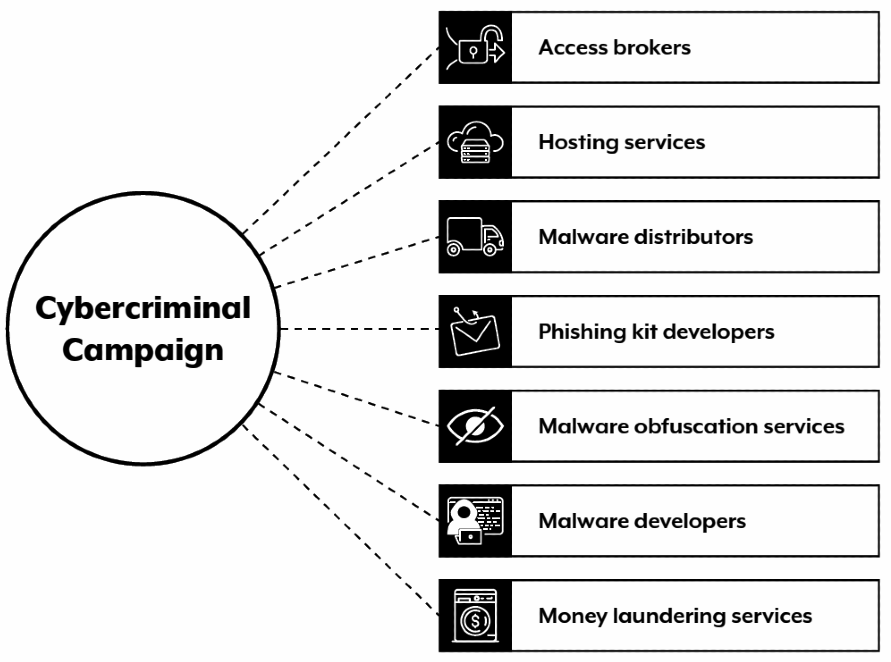
The Cybercrime-as-a-Service (CaaS) sector has also significantly reduced the barriers to entry for individuals looking to engage in cybercriminal activities.
Take, for instance, Ransomware-as-a-Service (RaaS), which offers opportunities for actors lacking technical expertise to launch highly lucrative ransomware attacks.
The CaaS industry also enables individuals to monetize their specialised skillsets. Consequently, cybercriminals have increasingly specialised during the 2021–22 period, presenting a heightened threat to both Australians and businesses.
Data Breaches in Australia
In 2022, while the Australian Cyber Security Centre received tens of thousands of cyberattack reports annually, two prominent companies, Optus, a leading telco, and Medibank, a private health insurer, faced large-scale cyberattacks that compromised millions of customers’ personal data.
These high-profile incidents underscore that the need for robust cybersecurity extends beyond large organisations. In fact, small and medium-sized businesses, as well as individual users, remain prime targets for cybercriminals.
The Price of Cyber Security In Australia
Over the past five years, the average cost of a data breach in Australia has surged by 32%, reaching a substantial AUD $4.03 million according to the 2023 Cost of a Data Breach Report.
A significant portion of breach costs, amounting to AUD $1.68 million, is attributed to detection and escalation expenses highlighting a notable shift toward more intricate breach investigations and response measures.
When considering breach costs by industry, the top three sectors in Australia with the highest average costs include Financial Services at AUD $5.56 million, Technology at AUD $5.06 million, and Education at AUD $4.61 million, all surpassing the national average of AUD $4.03 million.
Among the diverse cyber threats studied in Australia, phishing scams constituted over 22% of all breaches, while stolen or compromised credentials accounted for more than 17% of incidents.
The transformative impact of artificial intelligence (AI) and automation on breach identification and containment was evident.
Organisations that embraced these technologies witnessed faster response times, with Australian entities not utilising security AI and automation experiencing breaches that cost an average of AUD $2.14 million more than those who extensively deployed these solutions.
Furthermore, organisations leveraging both security AI and automation demonstrated a significantly shorter data breach lifecycle, reducing it by 117 days compared to those that had not implemented these technologies (225 days versus 342 days).
Regarding data storage environments, the most commonly breached data in Australia was distributed across multiple types of environments at 32%, followed by private cloud at 28%, and on-premises systems at 21%.
Throughout 2022, cybercriminals employed diverse tactics to attempt to gain access to personal information, resulting in tens of millions of Australian dollars in losses for victims.
Key Findings In The 2023 IBM Global Report
- The global average expense of a data breach in 2023 reached USD 4.45 million, marking a 15% uptick over the past three years.
- The report, conducted on a global scale, further revealed that 95% of examined organisations, including those in Australia, had encountered multiple breaches.
- Notably, organisations that fell victim to breaches were more inclined to shift incident costs onto consumers (57%) rather than boosting investments in security measures (51%).
Chief Technology Officer IBM Security, Asia Pacific Chris Hockings said, “In addition to reducing the time to identify and contain a data breach, the extensive use of security AI and automation is also a crucial factor in delivering significant cost savings to breached organisations in Australia.”

“In 2023, the industry is reaching a tipping point in the maturity curve for AI in security operations where enterprise grade AI capabilities can be trusted and automatically acted upon via orchestrated response,”
“This will unlock tangible benefits for speed and efficiency, which are desperately needed in today’s business landscape where early detection and fast response can significantly reduce the impact and losses from breaches,” said Hockings
The evolving landscape of technology has interconnected our world more than ever before, offering cybercriminals ever-expanding opportunities to exploit vulnerabilities.
Despite the continuous expansion of cybersecurity software and practices to meet growing demands, cybercriminals persist in their quest to identify weaknesses.
To address this ongoing threat, fostering cyber awareness and implementing fundamental security measures becomes imperative. This applies not only to corporations but also to individuals.
The Critical Infrastructure Threat
The ongoing concern regarding cyber threats to Australia’s critical infrastructure stems from the fact that the nation’s societal and economic well-being hinges on the seamless operation of these vital assets.
Critical infrastructure encompasses physical facilities, communication networks, as well as information and operational technologies that are essential for providing crucial services.
Disruptions within any part of this critical infrastructure ecosystem can have far-reaching consequences across the economy, potentially resulting in harm or loss of life, as exemplified by international ransomware attacks on healthcare services.
There persists a possibility that both state actors and cybercriminals may inflict similar disruptions by targeting critical infrastructure entities in Australia.
In the period of 2021-22, there was a notable surge in cyberattacks targeting critical infrastructure networks worldwide. Russia, in particular, aggressively targeted Ukraine’s critical infrastructure, employing destructive malware against high-voltage electrical substations.
Nevertheless, this threat is not confined to Ukraine alone, as some cybercrime groups aligned with Russia, including those who have successfully targeted Australian critical infrastructure, have publicly declared their intent to carry out operations against Ukraine’s allies.
The risk to Australia’s critical infrastructure networks is undeniably genuine. In 2021, the Russia-aligned Conti ransomware group specifically targeted the corporate network of CS Energy, an electricity generator in Australia, as described in more detail below.
- Case Study: CS Energy
In 2021, the ICT network of CS Energy, a Queensland Government-owned electricity generator responsible for generating 10% of the national electricity market’s power supply, fell victim to a cyberattack orchestrated by the Conti ransomware group.
On November 27, 2021, CS Energy detected the ransomware attack on its corporate network and swiftly disconnected it from the external internet. Concurrently, the company activated its business continuity protocols.
In addition to notifying pertinent Australian Government and Queensland Government entities, CS Energy, an established partner of the ACSC (Australian Cyber Security Centre), collaborated closely with the ACSC’s incident response support and external experts to address the situation.
By implementing network segregation—a recommended measure for ensuring business continuity—CS Energy successfully isolated its operational technology systems from the affected corporate network.
The segregation ensured that the incident did not compromise critical operational technology systems, including those responsible for electricity generation. Importantly, the energy supply remained unaffected by the cyberattack.
This incident underscores the significance of network segmentation and underscores the necessity of having comprehensive incident response, business continuity, and disaster recovery plans in place.
Through prompt and decisive action, CS Energy, in partnership with commercial incident response and cybersecurity specialists, along with the ACSC, effectively mitigated the incident, highlighting the maturity of Australia’s cybersecurity sector.
Cyber Report Contributors – Australian Cybercrime Statistics
| Australian Signals Directorate ASD’s purpose is to defend Australia from global threats and help advance Australia’s national interests. ASD delivers intelligence, cyber security and offensive operations. | |
 | Australian Criminal Intelligence Commission The Australian Criminal Intelligence Commission (ACIC), as Australia’s national criminal intelligence agency, works with law enforcement partners to improve the nation’s ability to respond to crime. |
 | Australian Federal Police The Australian Federal Police (AFP) is responsible for enforcing Commonwealth criminal law; contributing to combating complex transnational, serious, and organised crime impacting Australia’s national security; |
 | Australian Security Intelligence Organisation The Australian Security Intelligence Organisation (ASIO) is Australia’s security intelligence service. It protects Australia and Australians from threats to their security, including terrorism, espionage, and interference in Australia’s affairs by foreign governments. |
| Defence Intelligence Organisation The Defence Intelligence Organisation co-leads the ACSC’s Cyber Threat Assessment team in partnership with ASD to provide the Australian Government with an all-source, strategic, cyber threat intelligence assessment capability. | |
 | Department of Home Affairs The Department of Home Affairs leads cyber security policy for the Australian Government, including developing Australia’s Cyber Security Strategy 2020 and overseeing its implementation. |
Australian Cyber Report Summary
Throughout the year 2021–22, the Australian Cyber Security Centre (ACSC) collaborated with its partners on five successful operations targeting criminal online marketplaces and foreign scam networks.
While offshore cybercrime groups have targeted Australian victims, the threat from individual actors, including Australian citizens, persists. Australian law enforcement agencies have harnessed international alliances to combat criminal activities on a global scale.
In a rapidly evolving digital landscape, where cyber threats loom larger than ever, the release of the latest Australian Cyber Crime Statistics promises to be a significant milestone in understanding and combating the challenges faced by individuals and organisations.
Moving Forward – Cyber Crime In 2024
Spike in data breaches puts Australian Government agencies in spotlight
The OAIC noted that the Australian Government reported the second highest number of data breaches of all sectors, its highest position ever, though it has previously featured in the top five breached sectors. According to the report:
- Government agencies reported 63 data breaches from January to June 2024, accounting for 12% of all data breach notifications in Australia.
- The Government accounted for the highest number of social engineering or impersonation-style data breaches, making up 42% of such incidents.
- According to the OAIC, the breaches typically involved a threat actor impersonating a customer to gain access to an account using legitimate credentials.
- The Government is also slower to act: it had the largest proportion (87%) of notifications where the agency identified the incident over 30 days after it occurred, while 78% of Government notifications were made more than 30 days after the agency became aware of the incident.
The latest Notifiable Data Breaches Report from the Office of the Australian Information Commissioner (OAIC) shows a sharp rise in data breaches across the country during the first half of 2024.
With a 9% increase compared to the last half of 2023, it’s the highest number of reported breaches since 2020.. Released in September, the report highlights serious incidents like the MediSecure breach, which impacted 12.9 million Australians.
In response, the OAIC is taking a firmer approach on data privacy, warning that organisations need to put privacy at the forefront of their data management practices.







